
In the ever-evolving landscape of cybersecurity, websites face an increasing number of sophisticated threats. Protecting websites from these attacks is crucial for ensuring their integrity, availability, and user trust. Cloudflare’s Content Delivery Network (CDN) is a powerful tool that not only enhances website performance but also offers robust security features that protect websites from a wide range of cyber threats.
In this article, we’ll explore the primary security features integrated into Cloudflare’s CDN and how they safeguard websites from malicious attacks.
1. DDoS Protection
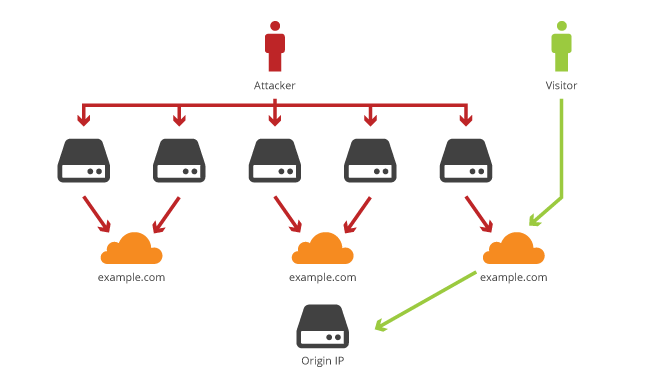
Distributed Denial-of-Service (DDoS) attacks are among the most common and damaging threats faced by websites. In a DDoS attack, attackers flood a website with massive amounts of traffic, overwhelming its resources and causing it to crash. Cloudflare’s CDN provides industry-leading DDoS protection that operates across multiple layers of the OSI model (Layers 3, 4, and 7). With a global network of data centers, Cloudflare can absorb and mitigate DDoS attacks of any size.
By utilizing Cloudflare’s DDoS protection, websites are shielded from attacks without affecting the performance of legitimate users. Cloudflare’s extensive capacity and intelligent routing ensure that traffic is distributed efficiently, and only malicious traffic is blocked, while legitimate requests are allowed to pass through.
Technical Advice: To maximize Cloudflare’s DDoS protection, ensure that your DNS settings are configured properly and that you enable automatic DDoS mitigation for both Layer 3 and Layer 7 attacks. This allows Cloudflare to protect your website from the moment the attack begins, without any additional configuration.
2. Web Application Firewall (WAF)
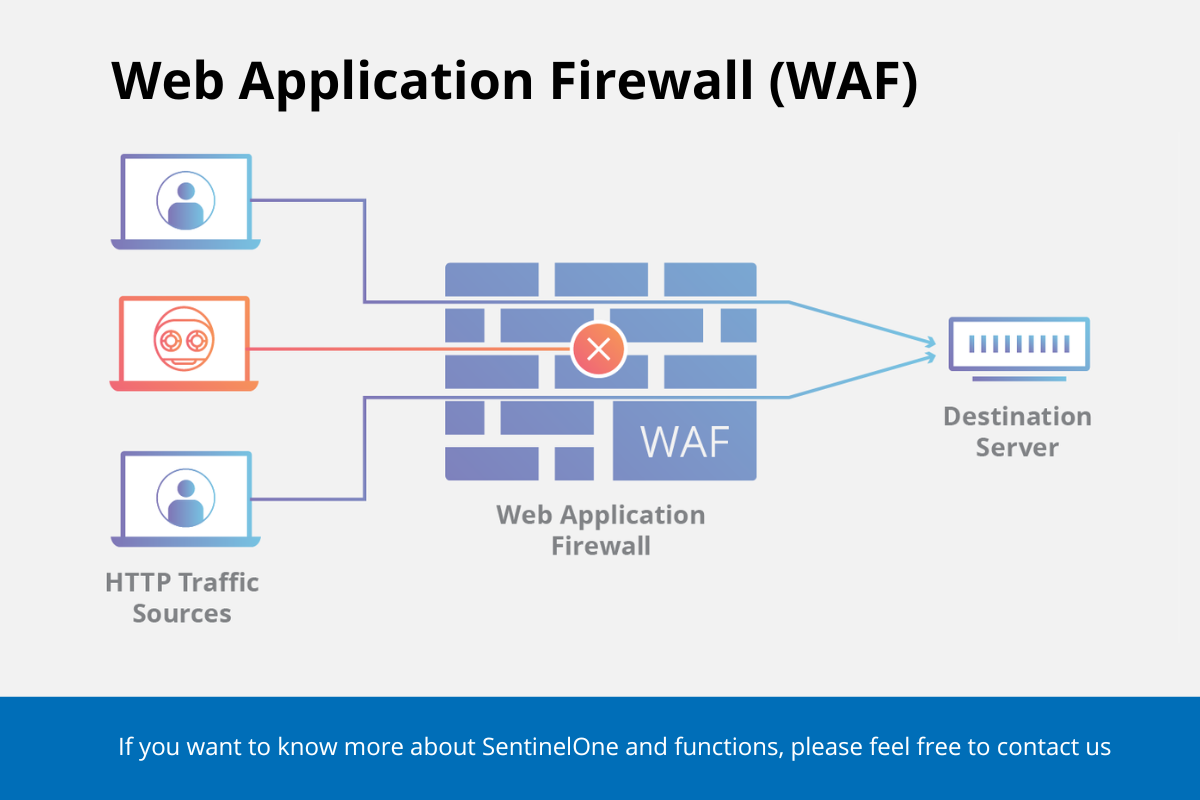
Web Application Firewalls (WAFs) play a crucial role in protecting websites from various threats, including SQL injection, cross-site scripting (XSS), and other vulnerabilities outlined in the OWASP Top 10. Cloudflare’s WAF is one of the key security features of its CDN, providing automatic protection against known vulnerabilities and real-time attack detection.
Cloudflare’s WAF is powered by a comprehensive rule engine that is constantly updated with threat intelligence from millions of websites protected by Cloudflare. It enables the creation of custom rules to tailor the protection according to specific website needs. The WAF actively inspects all incoming web traffic and blocks harmful requests while allowing legitimate ones to pass through seamlessly.
Technical Advice: Regularly review and update the WAF rules according to the changing threat landscape. Cloudflare provides automatic rule updates, but it’s advisable to create custom rules based on the specific needs of your website or web application to prevent zero-day attacks.
3. SSL/TLS Encryption
In today’s digital age, ensuring the security of data in transit is paramount. Cloudflare offers SSL/TLS encryption to secure the communication between a website and its visitors. By encrypting the data exchanged between users and the website, Cloudflare prevents attackers from intercepting and tampering with sensitive information, such as login credentials or payment details.
Cloudflare provides free SSL/TLS certificates, and the encryption is automatically enabled for websites using its CDN. This ensures that all data transmitted to and from the website is encrypted, making it significantly harder for attackers to conduct man-in-the-middle (MITM) attacks or eavesdrop on communications.
Technical Advice: Always enable HTTP/2 or HTTP/3 in conjunction with SSL/TLS to take advantage of performance improvements. Ensure that the SSL/TLS certificates are updated regularly, and that you’re using the highest level of encryption (TLS 1.2 or TLS 1.3) to maximize security.
4. Bot Mitigation
Bots are automated programs that can be used for malicious purposes, including web scraping, credential stuffing, and spamming. These bots can significantly degrade website performance, steal data, and compromise security. Cloudflare’s Bot Management feature uses a combination of machine learning, JavaScript challenges, and fingerprinting to identify and mitigate bot traffic.
Cloudflare assigns a “bot score” to incoming requests, categorizing them as human or bot traffic. If a request is flagged as coming from a malicious bot, Cloudflare can block or challenge the request using CAPTCHA or JavaScript challenges. This ensures that only legitimate human visitors are able to access the website.
Technical Advice: Configure Cloudflare’s Bot Management to block or challenge requests that come from high bot scores. Use “Rate Limiting” in conjunction with Bot Mitigation for added security against bot-based attacks.
5. Rate Limiting
Rate limiting is an effective security measure that prevents abuse by restricting the number of requests a user or bot can make to a website within a certain timeframe. Cloudflare’s rate limiting feature allows website administrators to define thresholds for specific URLs or resources. When a user exceeds these thresholds, Cloudflare automatically blocks or throttles their requests.
Rate limiting is particularly useful for preventing brute-force attacks, where attackers attempt to guess login credentials by submitting multiple incorrect login attempts in a short period. By limiting the number of requests that can be made to sensitive areas of the site, such as login forms or payment pages, rate limiting helps mitigate such attacks and protects the website from unauthorized access.
Technical Advice: Set up rate limits for sensitive endpoints, such as login pages or payment gateways, with a lower threshold to avoid brute-force attacks. Also, monitor the rate limiting logs to detect unusual traffic patterns that may indicate an ongoing attack.
Read more: How a CDN Can Drive Revenue Growth for Your Business
6. API Shield
APIs are critical components of modern websites, but they are also vulnerable to various security threats, including abuse, data breaches, and DoS attacks. Cloudflare’s API Shield provides security specifically designed to protect APIs from malicious traffic.
API Shield uses a positive security model, where only valid API traffic is allowed based on predefined schema validation, mutual TLS (mTLS), and JSON Web Token (JWT) validation. It also provides rate limiting and abuse detection to prevent excessive requests to the API. By implementing these protections, Cloudflare ensures that only trusted users and applications can access API endpoints securely.
Technical Advice: Enable mTLS for API endpoints where possible to ensure that only authorized clients can access the API. Regularly review the API logs to detect any signs of abuse or unauthorized access attempts.
7. Under Attack Mode
When a website is under an active attack, Cloudflare’s Under Attack Mode provides an additional layer of protection. This mode challenges visitors with an extra security check, such as a JavaScript challenge or CAPTCHA, before granting access to the website.
Under Attack Mode is particularly useful during large-scale attacks, such as DDoS or malicious bot activity, where it’s important to distinguish between legitimate users and malicious traffic. Cloudflare applies this mode automatically when a website is under a serious attack, ensuring that only legitimate users can access the site while blocking harmful traffic.
Technical Advice: When enabling Under Attack Mode, communicate to users that additional security challenges will be presented to ensure they understand the process. Use this mode sparingly, as it can impact the user experience.
8. Page Shield
Page Shield is a security feature that protects websites from client-side attacks, such as those targeting JavaScript files. This feature detects malicious or unauthorized changes to JavaScript code and alerts the website owner if anything suspicious is found.
By ensuring that JavaScript libraries on the website are secure, Cloudflare helps prevent common vulnerabilities like cross-site scripting (XSS) and clickjacking, which can lead to data theft, site defacement, and other security breaches.
Technical Advice: Enable Page Shield to monitor and protect your website’s JavaScript libraries from unauthorized changes. Regularly update and audit your scripts to reduce the chances of introducing vulnerabilities.
Conclusion
Cloudflare’s CDN provides a comprehensive suite of security features designed to protect websites from a wide range of cyber threats. From DDoS protection and WAF to bot mitigation and SSL/TLS encryption, Cloudflare offers an all-encompassing solution to safeguard websites, improve performance, and ensure a seamless user experience. As cyber threats continue to evolve, leveraging these advanced security features is essential for maintaining the integrity and availability of websites on the internet. By integrating Cloudflare’s CDN, website owners can rest assured that their online presence is well-defended against malicious attacks.
If you want to Configure and integrated Cloudflare CDN, feel free contact us for the details.



