In a remarkable demonstration of cybersecurity resilience, Cloudflare successfully thwarted the largest Distributed Denial-of-Service (DDoS) attack ever recorded, peaking at an unprecedented 7.3 terabits per second (Tbps). This monumental attack not only shattered previous records but also highlighted the growing sophistication of cyber threats and the critical need for robust defense mechanisms.
The Scale of the Attack
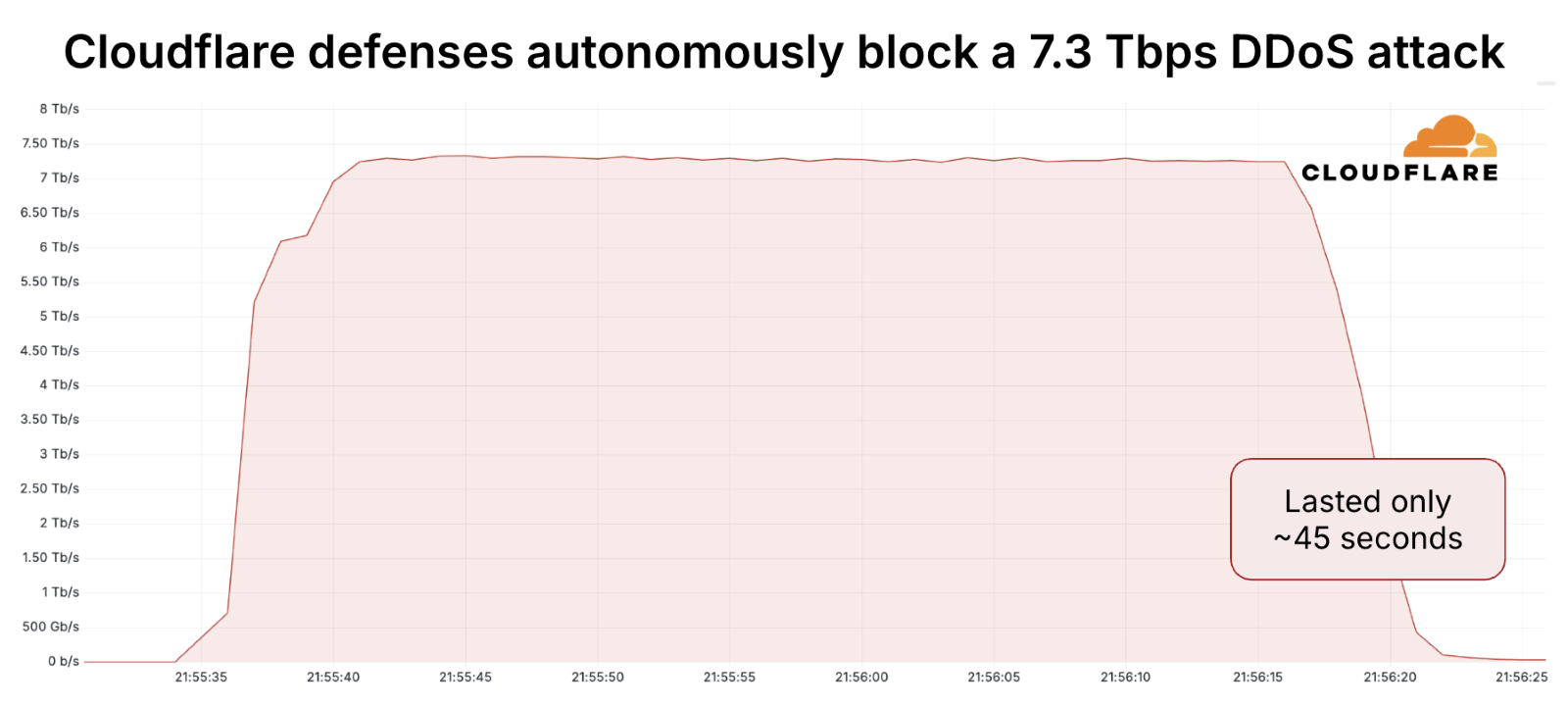
The attack took place in mid-May 2025, targeting a Cloudflare customer, a hosting provider utilizing Magic Transit to safeguard their IP network. Over the course of just 45 seconds, the cybercriminals unleashed a staggering 37.4 terabytes of data, equivalent to streaming over 9,350 full-length HD movies or downloading approximately 9.35 million songs. The sheer volume of data was enough to overwhelm most network infrastructures, but Cloudflare’s advanced security systems stood strong.
37.4 terabytes may not sound enormous in today’s data-heavy world but delivering that amount in just 45 seconds is a different story. To put it into perspective, that’s like downloading over 9,350 full-length HD movies in the blink of an eye or streaming a solid 7,480 hours of high-definition video non-stop. For context, that’s nearly an entire year of non-stop binge-watching. If it were music, you’d be downloading 9.35 million songs in less than a minute, enough to keep a listener occupied for 57 years straight.
Imagine snapping 12.5 million high-resolution photos on your smartphone without ever worrying about running out of space. If you took one shot every day, you’d still need 4,000 years to fill up that storage—yet all of this could happen in just 45 seconds. It’s not just a flood of data; it’s a storm of information that shows the sheer power of modern cyber threats.
Attack Vectors and Techniques And Details
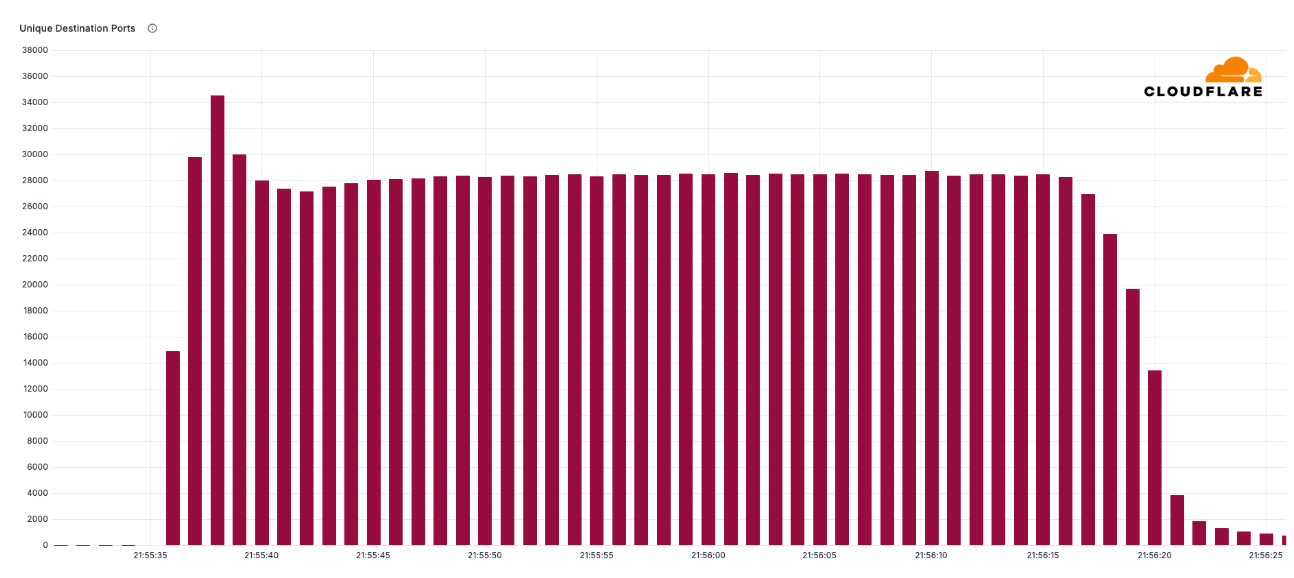
In this record-breaking DDoS attack, multiple attack vectors were employed to overwhelm the targeted infrastructure. The attack unleashed a relentless barrage, targeting an average of 21,925 destination ports on a single IP address used by our customer, with the assault peaking at 34,517 destination ports per second. This overwhelming flood of data came from a similarly widespread array of source ports, amplifying the sheer scale and complexity of the attack. It wasn’t just a single-point strike—it was a widespread, coordinated effort to flood the network with traffic from multiple angles, making it much harder to defend against.
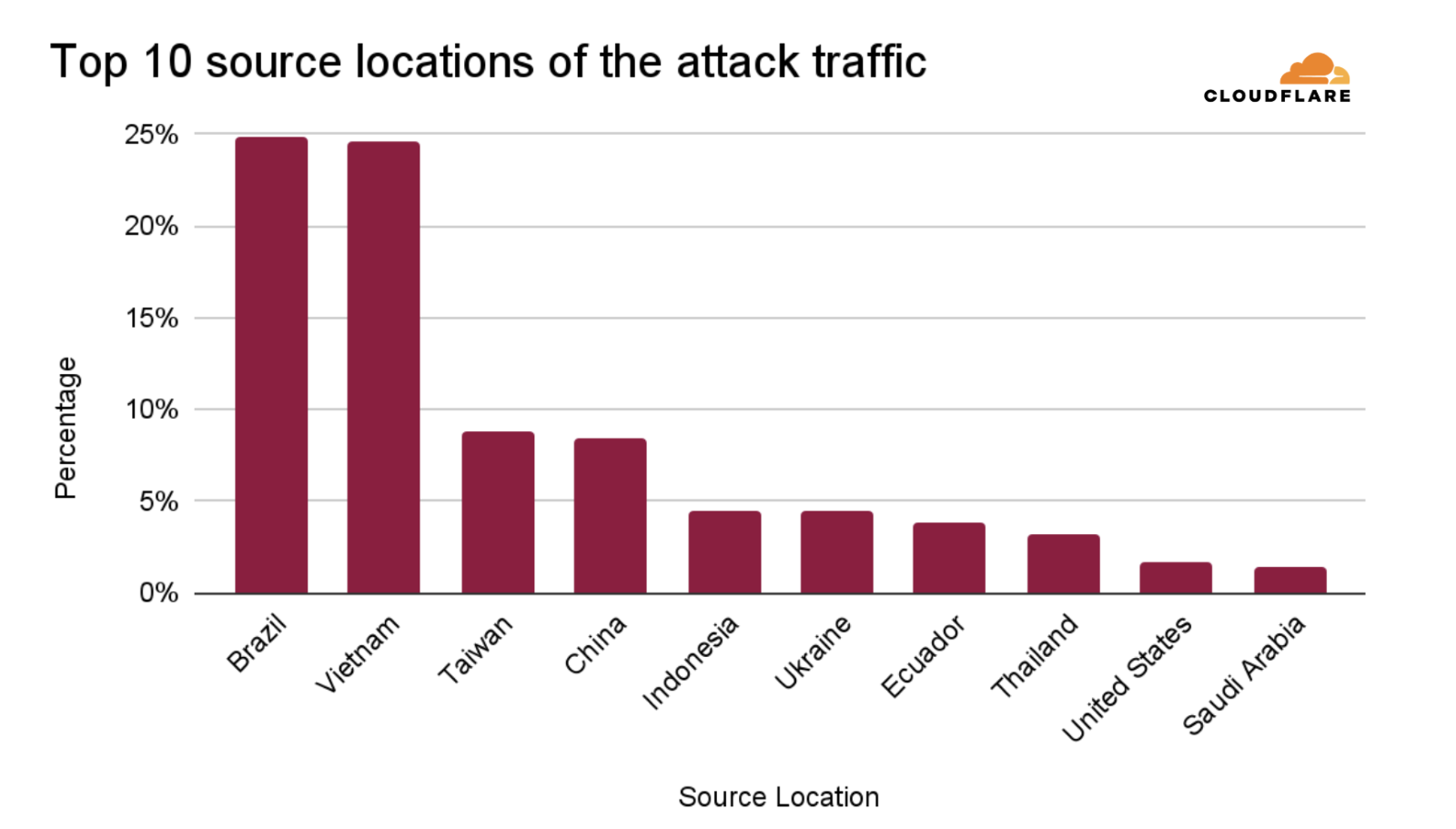
This DDoS attack was a multi-vector assault, with 99.996% of the malicious traffic consisting of UDP floods. These types of attacks send massive amounts of traffic to a target, aiming to overwhelm its resources and make services unavailable. The remaining 0.004% of the attack employed reflection and amplification techniques, such as QOTD, Echo, NTP, Mirai UDP flood, Portmap flood, and RIPv1 amplification, all designed to further magnify the volume of traffic hitting the target.
Cloudflare’s Mitigation Strategy : Leveraging Distributed Networks and Autonomous Detection
Cloudflare’s cutting-edge security infrastructure played a pivotal role in mitigating this massive attack. Thanks to the company’s advanced automated systems, the attack was detected and neutralized without any human intervention.
Cloudflare’s ability to absorb and mitigate such a colossal influx of traffic underlines the power and effectiveness of its DDoS protection measures. The company’s global network, which spans across multiple data centers worldwide, played a crucial role in distributing the load and ensuring the targeted network remained operational.
How the Attack Was Detected and Mitigated:
The magnitude and complexity of this attack required advanced detection and mitigation systems, powered by Cloudflare’s global infrastructure. Here’s how Cloudflare used its distributed nature and cutting-edge technology to detect, analyze, and mitigate the attack with minimal disruption:
1. Using the Distributed Nature of DDoS Attacks Against It
To combat the massive scale of the attack, Cloudflare leveraged global anycast to route the malicious traffic across multiple data centers worldwide. By advertising the attacked IP address from Cloudflare’s network, the attack packets were routed to the closest Cloudflare data center. This not only allowed the attack traffic to be dispersed but also used the inherent distributed nature of the DDoS attack to Cloudflare’s advantage.
As the traffic flooded in, it was mitigated in 477 data centers across 293 locations around the globe. In regions with high traffic, Cloudflare maintained multiple data centers to ensure traffic could be efficiently distributed and absorbed. This global presence helped mitigate the attack close to the source—at the network’s edge—ensuring that the target services remained online and unaffected.
2. Autonomous DDoS Detection and Mitigation
One of the key features of Cloudflare’s defense system is its autonomous DDoS detection and mitigation capabilities. Cloudflare’s security systems run in every data center, meaning attacks can be detected and mitigated autonomously, no matter where they originate from. This decentralization of defenses ensures rapid responses to emerging threats without human intervention.
Once an attack is detected, Cloudflare’s systems immediately begin to analyze and process the traffic. This enables the infrastructure to automatically identify and neutralize the threat without requiring manual involvement from operators, ensuring fast and efficient mitigation.
3.Real-Time Fingerprinting and Analysis
Cloudflare uses real-time fingerprinting to quickly identify and mitigate attack patterns. As packets enter Cloudflare’s data centers, they are intelligently load-balanced and sampled from within the Linux kernel’s eXpress Data Path (XDP). Using the extended Berkeley Packet Filter (eBPF), Cloudflare gathers packet samples and routes them to user space for analysis.
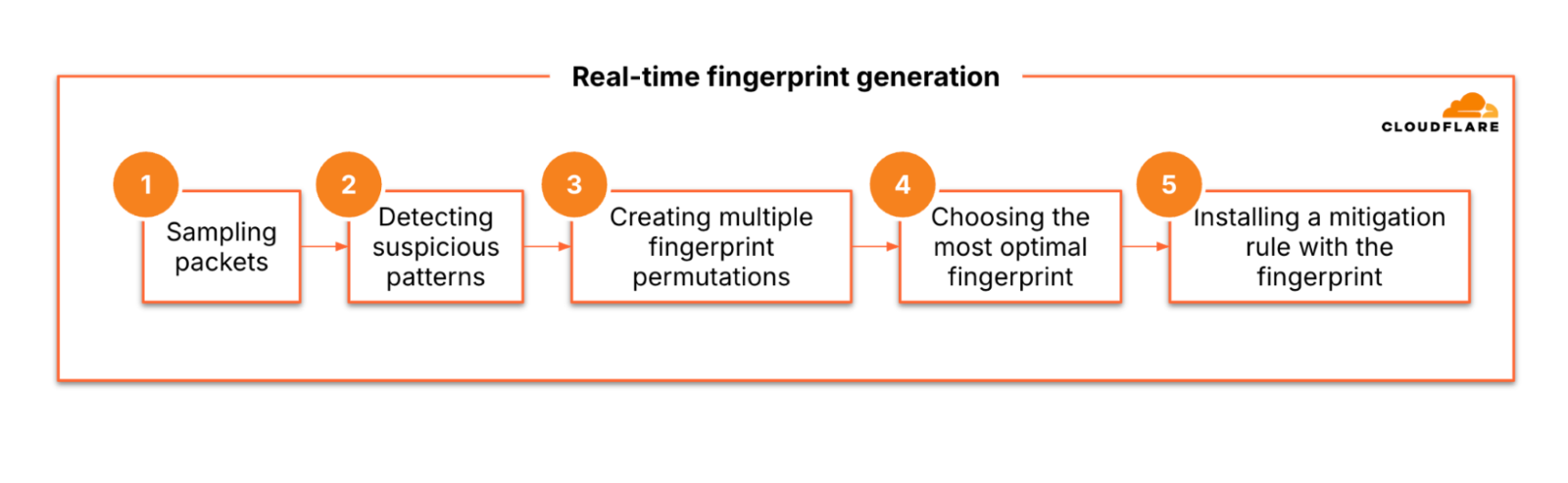
The samples are then analyzed by dosd, Cloudflare’s proprietary Denial of Service Daemon, which looks for suspicious patterns in the packet headers and identifies packet anomalies. Dosd applies unique heuristic techniques to detect attack patterns based on commonalities in the traffic. Once suspicious patterns are identified, dosd generates multiple fingerprint permutations to fine-tune the match and ensure precise identification of attack traffic.
This fingerprinting process is encapsulated within Cloudflare’s DDoS Protection Managed Rulesets, which are user-friendly rules applied automatically. The system continuously adjusts, generating new fingerprints and testing them against incoming traffic to ensure the highest mitigation accuracy without affecting legitimate users.
4. Dynamic Mitigation Process
Once a fingerprint with the most matches is identified, Cloudflare applies a data streaming algorithm to count how many packets match the attack pattern. When the activation threshold is met, a mitigation rule is triggered. This rule is compiled as an eBPF program that actively drops the attack packets. When the attack subsides, the rule times out and is automatically removed, ensuring minimal impact on normal traffic.
5. Gossiping for Better Defense: Real-Time Threat Intelligence
Cloudflare’s network is designed for efficiency and resilience. Each server autonomously detects and mitigates attacks, but it also shares real-time threat intelligence with other servers through gossiping (multicasting). This ensures that successful attack patterns, once identified, are shared across global data centers. The result is that threat intelligence is continuously refined, improving the system’s ability to detect and mitigate attacks in real time, both within a data center and globally.
6. Protecting the Internet: A Fully Autonomous Defense
This attack, which peaked at a monumental 7.3 Tbps, was successfully blocked without human intervention, alerts, or any service interruptions, demonstrating the power and precision of Cloudflare’s DDoS protection systems. The system automatically detected and mitigated the attack, preventing any disruptions to the customer’s services.
Cloudflare’s mission is to build a better, more secure internet, and its systems played a key role in maintaining that goal during this unprecedented DDoS assault. As part of this mission, Cloudflare provides free, unmetered DDoS protection to its customers, ensuring that the internet remains safe and accessible.
7. Cloudflare’s Connectivity Cloud: Protecting Your Network
Cloudflare’s connectivity cloud not only protects against DDoS attacks but also helps businesses build Internet-scale applications, accelerate websites, and defend against hackers. Whether it’s Zero Trust security or advanced DDoS protection, Cloudflare provides the tools to safeguard businesses and applications in an increasingly digital world.
For those looking to improve their internet security, you can start with Cloudflare’s free app at 1.1.1.1, which enhances both speed and security.
To learn more about Cloudflare’s mission to build a better internet, visit the official website, or explore open career positions to join the team that’s shaping the future of online security.
Read More : Cloudflare Recognized as a Strong Performer in Email Security by Forrester
The Growing Threat of DDoS Attacks
This event underscores the escalating scale of cyber threats facing organizations today. DDoS attacks are growing in both frequency and intensity, and they pose a serious risk to businesses, government entities, and critical infrastructure. As cybercriminals continue to refine their attack strategies, the need for comprehensive and effective DDoS defense solutions has never been more critical.
Organizations that rely on digital services must invest in robust cybersecurity measures to protect their infrastructure from similar threats. The Cloudflare incident serves as a stark reminder that a single well-coordinated attack can have the potential to disrupt services, cause financial losses, and damage reputations. As we continue to move toward an increasingly connected world, preparing for large-scale cyberattacks is not just important—it’s essential. If your organization is looking to enhance its cybersecurity defenses, ANP Technology can help. We provide advanced DDoS protection and a range of cutting-edge security solutions designed to safeguard your infrastructure from emerging threats.
Conclusion
Cloudflare’s successful defense against this unprecedented DDoS attack not only showcases the company’s advanced technological capabilities but also highlights the urgent need for comprehensive cybersecurity strategies in the face of evolving threats. As we move forward, organizations must be proactive in building resilient networks and deploying advanced security systems to defend against the growing risk of cyberattacks. The world of cybersecurity is constantly evolving, and Cloudflare’s latest success story demonstrates that staying ahead of the curve is vital in keeping the internet secure.
Contact us today to learn how we can help you build a secure, resilient system that stands strong against the growing wave of cyberattacks. Your digital security is our top priority. Let us help you protect your business from the next major cyber threats.



