While this report primarily focuses on 2025 Q1, it also includes late-breaking data from a hyper-volumetric DDoS campaign observed in April 2025, featuring some of the largest attacks ever publicly disclosed. In a historic surge of activity, we blocked the most intense packet rate attack on record, peaking at 4.8 billion packets per second (Bpps), 52% higher than the previous benchmark, and separately defended against a massive 6.5 terabits-per-second (Tbps) flood, matching the highest bandwidth attacks ever reported.
Key DDoS insights
- In the first quarter of 2025, Cloudflare blocked 20.5 million DDoS attacks. That represents a 358% year-over-year (YoY) increase and a 198% quarter-over-quarter (QoQ) increase.
- Around one third of those, 6.6 million, targeted the Cloudflare network infrastructure directly, as part of an 18-day multi-vector attack campaign.
- Furthermore, in the first quarter of 2025, Cloudflare blocked approximately 700 hyper-volumetric DDoS attacks that exceeded 1 Tbps or 1 Bpps — an average of around 8 attacks per day.
All the attacks were blocked by our autonomous defenses.
DDoS attacks in numbers
In the first quarter of 2025, we blocked 20.5 million DDoS attacks. For comparison, during the calendar year 2024, we blocked 21.3 million DDoS attacks. In just this past quarter, we blocked 96% of what we blocked in 2024.
The most significant increase was in network-layer DDoS attacks. In 2025 Q1, we blocked 16.8M network-layer DDoS attacks. That’s a 397% QoQ increase and a 509% YoY increase. HTTP DDoS attacks also increased — a 7% QoQ increase and a 118% YoY increase.
We count DDoS attacks based on unique real-time fingerprints generated by our systems. In some instances, a single attack or campaign may generate multiple fingerprints, particularly when different mitigation strategies are applied. While this can occasionally lead to higher counts, the metric offers a strong overall indicator of attack activity during a given period.
Attack size & duration
Despite the increase in hyper-volumetric attacks, most DDoS attacks are small. In 2025 Q1, 99% of Layer 3/4 DDoS attacks were under 1 Gbps and 1 Mpps. Similarly, 94% of HTTP DDoS attacks were 1 million requests per second (rps). However, ‘small’ is a relative term and most Internet properties wouldn’t be able to withstand even those small attacks. They can easily saturate unprotected Internet links and crash unprotected servers.
Furthermore, most attacks are very short-lived. 89% of Layer 3/4 DDoS attacks and 75% of HTTP DDoS attacks end within 10 minutes. Even the largest, record-breaking, hyper-volumetric DDoS attacks can be very short, such as the 35-second attack seen in the examples above. 35 seconds, or even 10 minutes, is not a sufficient time for manual mitigation or activating an on-demand solution: by the time a security analyst receives the alert, and analyzes the attack, it’s already over. And while the attacks may be very short, the trickle effect of attack leads to network and applications failures that can take days to recover from — all whilst services are down or degraded. The current threat landscape leaves no time for human intervention. Detection and mitigation should be always-on, in-line and automated — with sufficient capacity and global coverage to handle the attack traffic along with legitimate peak time traffic.
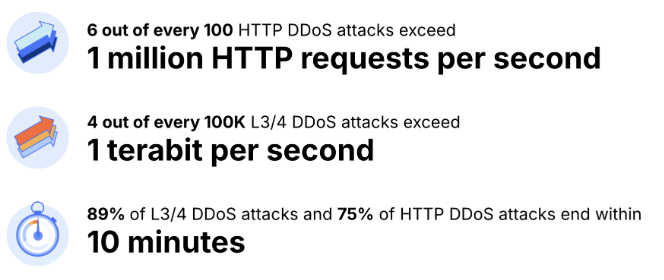
On the other hand, hyper-volumetric HTTP DDoS attacks that exceed 1 Mrps doubled their share. In 2025 Q1, 6 out of every 100 HTTP DDoS attacks exceeded 1 Mrps. On the network-layer, 1 out of every 100,000 attacks exceeded 1 Tbps or 1 Bpps.
Read the full report from here:https://blog.cloudflare.com/ddos-threat-report-for-2025-q1/
If you would like to know more about Cloudflare, welcome to contact us online.



