In Australia’s rapidly growing digital landscape, businesses and organizations increasingly depend on online services to conduct their operations. However, this reliance also introduces new challenges, especially regarding cybersecurity. One of the most significant threats to Australia’s online infrastructure is the rise of Distributed Denial of Service (DDoS) attacks, which have become an important concern for organizations across various industries.
These attacks can cause significant disruptions, lead to downtime, and impact a company’s reputation. This is where DDoS protection becomes crucial.
In this article, we’ll explore what DDoS protection is, why it’s necessary, and how to anticipate and defend against these attacks.
What is a DDoS Attack?
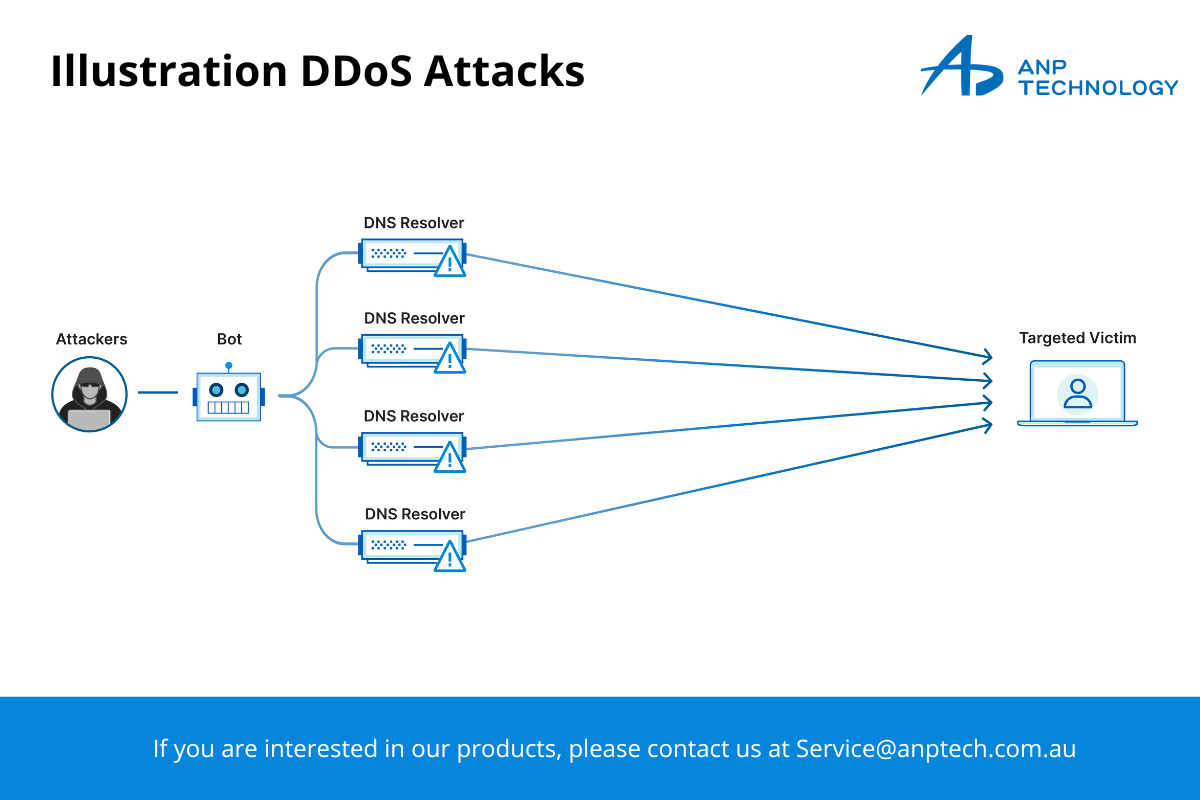
A Distributed Denial of Service (DDoS) attack is a cyber-attack where multiple systems (often compromised devices) are used to flood a target system with traffic, overwhelming the system’s resources and causing it to become slow, unresponsive, or completely unavailable.
Unlike traditional Dos (Denial of Service) attacks launched from a single source, DDoS attacks are distributed, meaning they come from various sources, making them harder to mitigate. These attacks can be launched from thousands or even millions of devices, often unknowingly compromised and controlled by cybercriminals. This network of compromised devices is called a botnet.
Why is DDoS Protection Important?
DDoS attacks can have severe consequences for any organization, including:
- Service Disruptions: A DDoS attack can render a website or online service unavailable to users for hours or even days, causing revenue losses and damaging customer trust.
- Reputation Damage: Extended downtime or security breaches may harm your brand’s reputation. Customers and stakeholders might question your ability to ensure service continuity.
- Financial Loss: Besides potential lost revenue, the costs associated with mitigating an attack and recovering from the damage can be substantial.
- Legal and Regulatory Consequences: In some cases, prolonged service disruptions may lead to legal and regulatory requirements, resulting in fines or penalties.
The History of DDoS Attacks
DDoS attacks have evolved over the years, becoming more sophisticated and widely used in cybercrime. Below is a timeline that highlights key moments in the history of DDoS attacks:
- 1990s – Early Beginnings: The concept of DDoS attacks emerged with the introduction of Smurf attacks. These attacks relied on compromised system networks to flood a target with traffic. In 1997, the first known DDoS attack was executed by a hacker named Mafiaboy on Yahoo!, one of the largest websites. This attack was among the first to demonstrate the vulnerability of large-scale websites to distributed attacks.
- 2000s – The Rise of DDoS Attacks: The early 2000s saw the rise of several powerful DDoS tools such as Trinoo and Stacheldraht, which made it easier for hackers to launch large-scale attacks using a botnet of compromised computers. A significant attack during this period was Mafiaboy’s attack on Yahoo!, which marked one of the first major disruptions to the Internet’s infrastructure.
During this time, many companies and government agencies started to realize the critical need for DDoS protection, leading to the development of DDoS mitigation services. - 2010s – Sophistication and Large-Scale Attacks: As internet infrastructures grew and became more complex, DDoS attacks evolved from simple bandwidth overloads to more targeted attacks, including those aimed at specific applications. In 2014, the GitHub DDoS attack reached 400 Gbps, demonstrating the power of reflection and amplification techniques in modern DDoS attacks.
- The Dyn DDoS attack in 2016, which used a botnet of Internet of Things (Iot) devices, marked a significant turning point. The attack disrupted services for major websites like Twitter, Spotify, and Netflix, showing how unsecured Iot devices could be leveraged to launch large-scale attacks.
- 2020s – DDoS as a Service: Today, DDoS attacks continue to grow in scale and complexity. DDoS-as-a-Service platforms have made it easier for individuals without technical expertise to launch attacks for a fee. The availability of such services has democratized cyberattacks, enabling more attackers to carry out DDoS disruptions.
Modern DDoS attacks can reach multiple terabits per second, as seen in the largest attacks in recent years. This increase in attack size has led to a surge in demand for more advanced DDoS protection solutions.
How to Anticipate DDoS Attacks
DDoS attacks are often difficult to predict, but there are steps you can take to anticipate and reduce the risk:
- Monitor Traffic Patterns: Regularly monitor and analyze your website traffic. Anomalies, such as sudden spikes or unusual traffic patterns, may be early indicators of an impending attack.
- Threat Intelligence: Leverage threat intelligence services that track cyber threats globally. These can help identify attack trends and emerging threats, allowing you to take proactive measures.
- Understand Your Baseline: Establish a baseline for your network’s regular operation. Knowing what “normal” traffic looks like makes it easier to spot unusual surges that could be an early sign of a DDoS attack.
- Test for Vulnerabilities: Conduct regular security assessments and penetration testing to identify potential vulnerabilities in your system that could be exploited in a DDoS attack. ANP Technology offers comprehensive solutions to help you identify and test potential vulnerabilities in your system.
Read more: How to Handling Bot Traffic With Cloudflare Bot Management
How to Protect Against DDoS Attacks
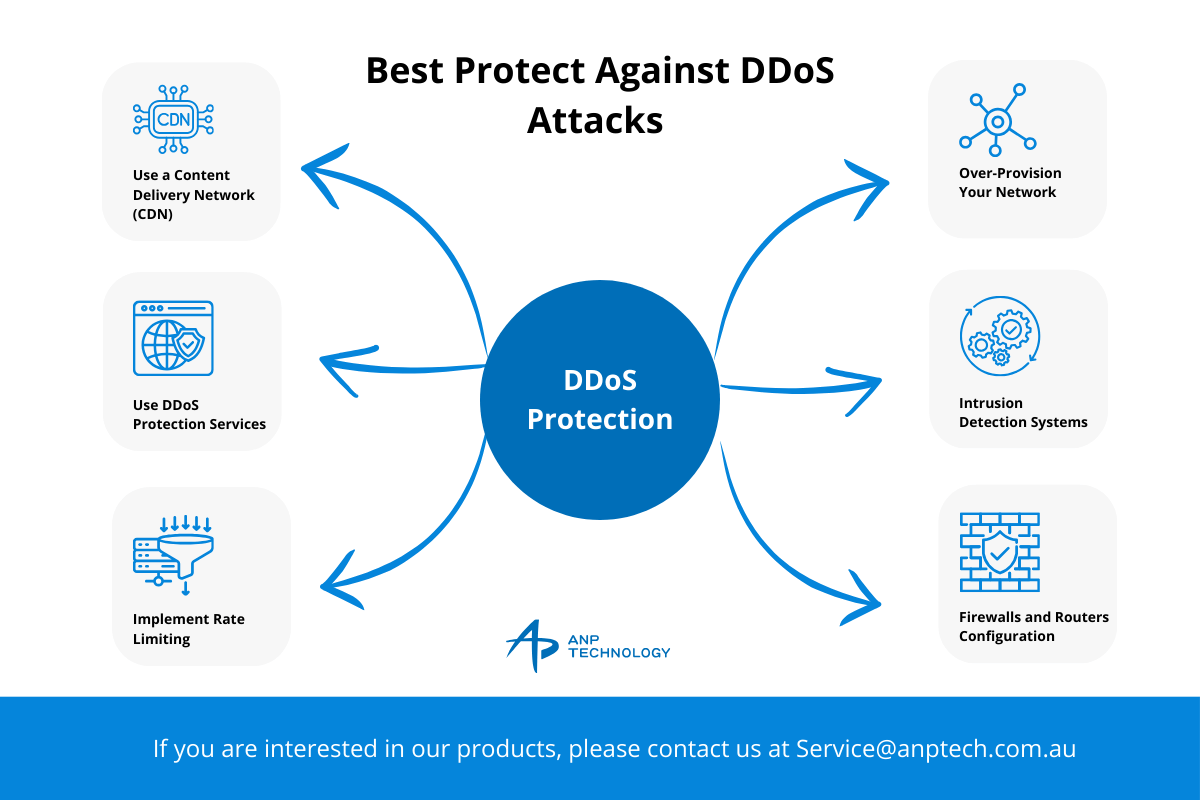
Once you’ve anticipated potential DDoS attacks, the next step is implementing protection measures. Here are some key strategies:
- Use a Content Delivery Network (CDN): CDNS can distribute traffic across multiple servers, thus reducing the risk of a DDoS attack overwhelming your servers. By caching content and serving it from distributed locations, CDNS make it more difficult for attackers to target your infrastructure.
- Implement Rate Limiting: Rate limiting controls how many requests a user can make to a server in a given time. Limiting the number of requests can reduce the chance of an attack overwhelming your server.
- Use DDoS Protection Services: Many services, such as Cloudflare and Amazon Web Services (AWS) Shield, provide advanced DDoS mitigation services. These services can absorb large-scale attacks by redirecting traffic through their networks and filtering malicious requests.
- Over-Provision Your Network: Ensure your infrastructure has more bandwidth and capacity than your standard requirements. Having excess capacity allows your system to handle sudden surges in traffic, making it more resilient to DDoS attacks.
- Intrusion Detection Systems (IDS): These systems can help detect abnormal traffic patterns and automatically trigger defensive measures. An IDS can identify when a DDoS attack starts and take immediate action, such as filtering out malicious traffic.
- Firewalls and Routers Configuration: Use advanced firewall configurations to block traffic from known malicious IP addresses. You can also configure routers to detect and mitigate some DDoS attacks, although this requires careful planning and expertise.
Conclusion
DDoS protection is no longer optional—it’s essential for maintaining the security and availability of online services. By anticipating potential attacks and implementing robust protection strategies, businesses can mitigate the impact of DDoS attacks, protect their reputation, and ensure that their services remain available to customers.
Adopting a proactive approach to security, including regular monitoring, threat intelligence, and leveraging DDoS protection services, will go a long way in safeguarding your organization from these potentially devastating attacks. Investing in DDoS protection not only secures your infrastructure but also provides peace of mind to your customers and stakeholders.

Protect Your Business from DDoS Attacks Today!
Don’t wait until your systems are compromised. Implementing DDoS protection is essential for ensuring the availability and security of your online services.
Contact us now to learn about our DDoS protection solutions.



