
In today’s rapidly evolving cybersecurity landscape, businesses are increasingly relying on advanced solutions to protect their critical systems, networks, and data from cyberattacks. As organizations continue to embrace digital transformation, traditional security tools may no longer be sufficient to defend against sophisticated threats. SentinelOne, an AI-driven endpoint protection platform, offers cutting-edge solutions to address these challenges by providing real-time threat detection, prevention, and automated response. However, for SentinelOne to be most effective, it should be seamlessly integrated into an organization’s existing security infrastructure.
Integrating SentinelOne with your security system can enhance your overall cybersecurity posture by ensuring that endpoint protection works in harmony with other tools such as firewalls, SIEM (Security Information and Event Management) systems, and network security solutions.
In this article, we will explore how to integrate SentinelOne with your security system, step-by-step, to create a unified defence strategy.
Why Integrate SentinelOne with Your Security System?
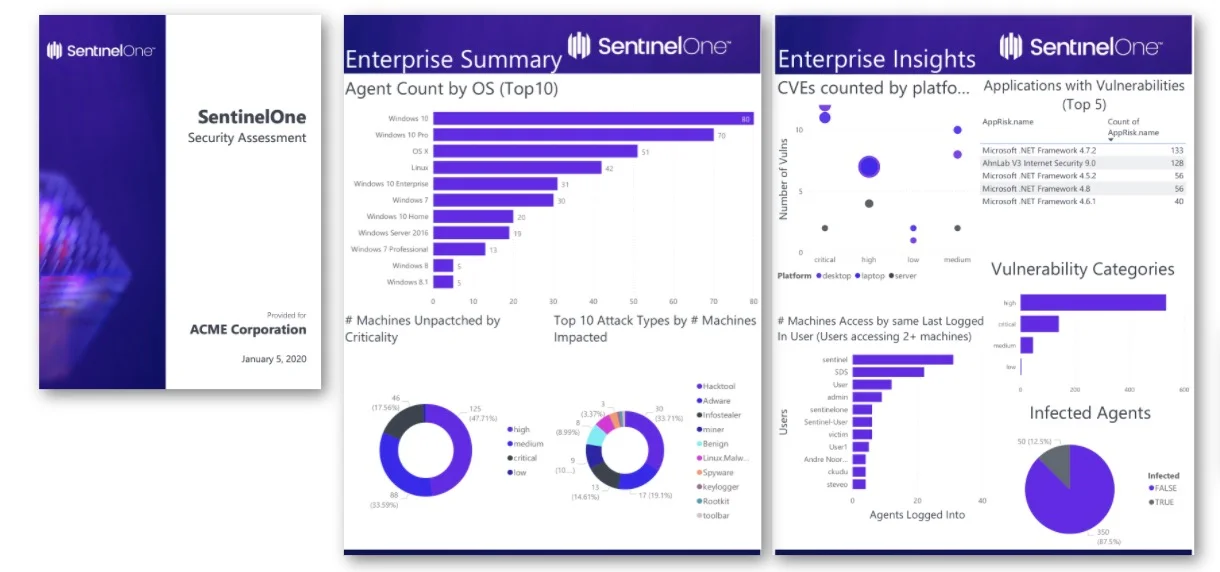
Integrating SentinelOne with your broader security infrastructure is crucial for several reasons:
- Enhanced Threat Detection and Response: By integrating SentinelOne with other tools, you enable cross-platform threat intelligence sharing. This ensures that your security system can detect, analyse, and respond to threats more quickly and efficiently.
- Centralized Management: Integration allows your security operations team to manage multiple security solutions from a single pane of glass, simplifying the monitoring and management process.
- Automated Incident Response: SentinelOne’s autonomous response capabilities can be leveraged alongside other security tools to automate incident response workflows, reducing the reliance on manual intervention.
- Improved Forensics and Reporting: Integration with SIEM systems and other tools ensures that all security events, including those detected by SentinelOne, are logged and available for forensics and reporting.
- Compliance and Auditing: Integrating SentinelOne with your security system helps ensure that your organization maintains compliance with industry regulations by providing accurate logs and reports of security events.
Read more: SentinelOne vs Anti Virus Traditional, Which is Better ?
Steps to Integrate SentinelOne with Your Security System
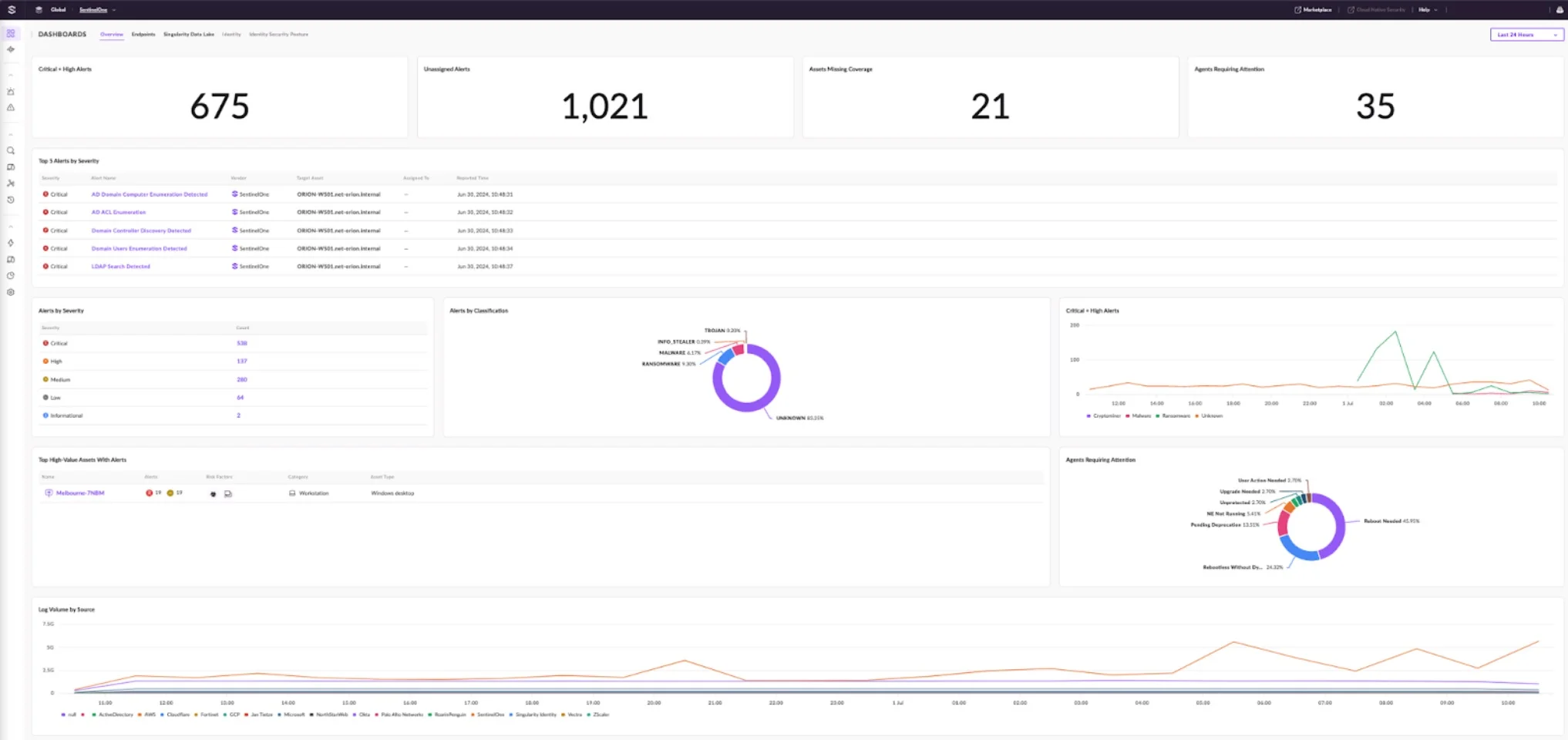
Integrating SentinelOne into your security system involves several key steps, which can be broadly categorized into preparation, integration, and testing. Let’s explore each step in more detail.
1. Preparation for Integration
Before integrating SentinelOne with your security system, there are several preparatory steps that need to be taken to ensure a smooth and successful integration:
- Review Your Existing Security Infrastructure: Assess your current security systems, including firewalls, antivirus, SIEM, network monitoring tools, and any other endpoint protection solutions. Identify the gaps in protection that SentinelOne will address and determine how it can complement your existing infrastructure.
- Check System Compatibility: Ensure that your operating systems, network devices, and security tools are compatible with SentinelOne. SentinelOne supports a wide range of operating systems, including Windows, macOS, Linux, and cloud environments, but you need to verify compatibility with your specific setup.
- Assign Roles and Permissions: Define roles and permissions within your security operations team. Decide who will have administrative access to SentinelOne and configure the necessary user access rights for managing the system.
- Prepare for Data Sharing: If you plan to integrate SentinelOne with a SIEM or other security platforms, ensure that those systems are configured to receive logs and event data from SentinelOne. This may require setting up API access or configuring log forwarding.
2. Integrating SentinelOne with Your Security System
Once preparations are complete, you can move on to integrating SentinelOne into your security infrastructure. The integration process will vary depending on the systems you are using, but here are some common integration methods:
a. Integrating SentinelOne with a SIEM System
SIEM systems, such as Splunk, IBM QRadar, or LogRhythm, aggregate and analyse security data from various sources, helping to identify and respond to security incidents. Integrating SentinelOne with your SIEM can provide a centralized view of your security posture.
To integrate SentinelOne with your SIEM system, follow these general steps:
- Enable SentinelOne API Access: SentinelOne provides API access to send security event data to external systems. Access the SentinelOne management console and configure the API settings for integration.
- Configure Log Forwarding: Depending on your SIEM solution, configure SentinelOne to forward security logs, including threat detection events and response actions, to your SIEM. This can be done by setting up log forwarding rules within the SentinelOne platform.
- Map SentinelOne Event Data to SIEM Fields: Once log forwarding is set up, map the event data from SentinelOne to the appropriate fields in your SIEM. This will allow your SIEM to interpret the data correctly and generate alerts or reports based on SentinelOne’s findings.
- Create Custom Dashboards: After integration, create custom dashboards in your SIEM system to display SentinelOne’s threat detection, response, and remediation actions. This will help your security team monitor SentinelOne’s performance alongside other security events.
b. Integrating SentinelOne with Firewalls and Network Security Tools
SentinelOne’s ability to prevent lateral movement of threats across the network can be enhanced by integrating it with network security solutions like firewalls and intrusion detection/prevention systems (IDS/IPS). Here’s how you can achieve integration:
- API Integration: Many modern firewalls and IDS/IPS solutions offer API access, which allows SentinelOne to trigger automatic network defences when a threat is detected. For example, if SentinelOne identifies a malicious process, it can trigger your firewall to block the associated IP addresses or domains.
- Automated Network Containment: When an attack is detected by SentinelOne, you can configure the platform to communicate with your firewall to automatically isolate compromised devices or limit the affected network segments. This containment action reduces the spread of the attack.
- Correlating Security Events: By integrating SentinelOne with your network security tools, you enable cross-platform event correlation. For example, if your firewall detects a suspicious incoming connection and SentinelOne identifies a related endpoint compromise, both events can be correlated, providing a more comprehensive view of the attack.
c. Integrating SentinelOne with Endpoint Detection and Response (EDR)
If your organization uses a separate EDR solution, you may want to integrate it with SentinelOne to enable a unified approach to endpoint security.
- Unified Incident Management: Integration between SentinelOne and your EDR solution ensures that threat data from both platforms is collected and analysed in one place. This allows security teams to identify complex multi-layered attacks more effectively.
- Automatic Response Actions: In some cases, you can set up automated response actions to complement SentinelOne’s capabilities. For example, when SentinelOne detects a threat, it can trigger your EDR system to apply additional mitigation measures, such as isolating the device from the network.
3. Testing the Integration
After integrating SentinelOne with your security system, it’s important to conduct thorough testing to ensure that everything is working as expected. Some key areas to test include:
- Event Data Flow: Verify that security event data is flowing correctly between SentinelOne and your SIEM, firewall, or other security tools. Test for both successful and failed event forwarding.
- Automated Incident Response: Test the automated response actions, such as isolating compromised endpoints or blocking malicious network connections. Ensure that these actions trigger as expected during a simulated attack.
- Threat Detection Accuracy: Perform simulated attacks (e.g., phishing or malware tests) to ensure that SentinelOne detects and responds to threats in real-time and that integrated systems react appropriately.
- Reporting and Dashboarding: Verify that the data from SentinelOne is correctly displayed on your SIEM dashboards and that the reports reflect accurate information about threat detection and response actions.
Conclusion
Integrating SentinelOne into your security system can significantly enhance your organization’s defence capabilities by providing proactive threat detection, real-time response, and automated recovery. By following the steps outlined in this article, you can ensure a seamless integration process with your existing security infrastructure, enabling you to respond to cyber threats quickly and efficiently.
Whether you’re integrating SentinelOne with SIEM platforms, firewalls, or endpoint security tools, this integration will empower your security teams to work more effectively and create a unified defence strategy that protects your organization from modern cyber threats.
If you want to Integrate SentinelOne with Your Security System contact us here for more information.



